
Explore the critical distinctions—and connections—between IT, cybersecurity, and compliance. While these areas often overlap and support one another, they also present unique challenges when aligning goals, responsibilities, and resources. Understanding these relationships is the first step toward building an effective Cybersecurity program. Join VMEC and Norwich University Applied Research Institutes (NUARI), our Cybersecurity partner, as we dive into strategies for developing a program over time, helping your organization strengthen security, maintain compliance, and create a resilient IT environment.
Welcome & Introduction
- Learning objectives:
-
- Understand the differences and overlap between IT, cybersecurity, and compliance
- Recognize challenges and opportunities in aligning these areas
- Learn practical steps to build a cybersecurity program over time
Understanding IT, Cybersecurity, and Compliance
- Definitions & Scope:
- IT: managing technology infrastructure, systems, and services
- Cybersecurity: protecting data, networks, and systems from threats
- Compliance: adhering to regulations, standards, and policies
- Third-party vendors: understanding services (e.g. MSSP, other SaaS,….) to determine compliance and standards
- How they overlap and support each other:
- IT provides the foundation for cybersecurity
- Cybersecurity helps ensure compliance requirements are met
- Compliance guides IT and cybersecurity priorities
- Challenges and friction points:
- Conflicting priorities (speed vs. security vs. compliance)
- Resource allocation and ownership
- Misaligned metrics or Key Performance Indicators
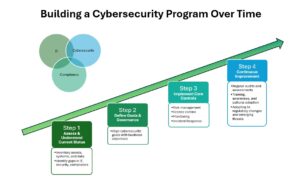
Building a Cybersecurity Program Over Time
- Step 1: Assess & Understand Your Organization
- Inventory assets, systems, and data
- Identify gaps in IT, security, and compliance
- Step 2: Define Goals & Standards
- Align cybersecurity goals with business objectives
- Establish roles, responsibilities, and policies
- Step 3: Implement Core Controls
- Risk management, access control, monitoring, incident response
- Risk management, access control, monitoring, incident response
- Step 4: Maintaining Compliance
- Regular audits and assessments
- Training, awareness, and cultural adoption
- Adapting to regulatory changes and emerging threats
Real-World Examples & Common Pitfalls
- Examples of successful integration of IT, cybersecurity, and compliance
- Lessons learned from common missteps:
- Ignoring compliance until it’s urgent
- Underestimating IT-cybersecurity coordination
- Failing to scale program with organizational growth
- Understanding MSSP engagements
Key Takeaways
- IT, cybersecurity, and compliance are distinct but interdependent
- Clear governance, risk awareness, and strategic alignment are essential
- Building a cybersecurity program is iterative and requires continuous improvement
Q&A and Closing
When registering, please add any specific comments or questions you wish to have addressed during this webinar in the Comments field.